Table of Contents
Introduction
This document describes the procedures and functionalities for installation and operation of the Secret Double Octopus iPhone Authenticator Mobile App, including:
- Secret Double Octopus iPhone App Installation
- User Enrollment
- Authentication Scenarios
- Mobile App Operation
Solution Overview
Secret Double Octopus conducts strong authentication without passwords, thereby eliminating user frustration caused by complex passwords and reducing support costs around password changes. Organizations benefit from high assurance and credential control across domain accounts, VPN, cloud applications, and legacy apps.
Secret Double Octopus iPhone Mobile Authentication
The mobile device, especially the iPhone, is an ideal authenticator. However, first-generation attempts at mobile authentication often suffered from a single point of failure. One example was the reliance on SMS for authentication, which was proven to be easily hack able. Similarly, other approaches, such as keys and push notifications, had vulnerabilities.
Secret Double Octopus introduced the industry’s first authenticator with multi-shield authentication for devices and users. The Secret Double Octopus iPhone solution is flexible enough to support any desktop, backend application, VPN, or cloud services, focusing on delivering the most seamless user experience possible.
Security benefits of the Secret Double Octopus solution include:
• Resilient, multi-shield device authentication: Secret Double Octopus presents a unique Secret Sharing cryptographic algorithm, resilient to unlimited computing power. The device is authentication through multiple routes, thus avoiding a single point of hacking.
• Complete multi-factor with biometrics: The Octopus Authenticator utilizes biometric systems such as Touch ID and FIDO, as well as identity access management systems like
Active Directory to conduct complete multi-factor verification in a single solution.
• Avoidance of MiTM Attacks and SSL manipulations: A random AES256 key is delivered to the device using Secret Sharing for symmetric encryption, eliminating MITM and eavesdropping attacks.
• Hardened Mobile App: The Octopus Authenticator Mobile App includes the following protections against cyber-attacks:
• Binary obfuscation
• Root/Jailbreak detection
• Anti-Tampering
• Code injection protection
• Device ID pinning
• MiTM protection
• Backup protection
• Encrypted file system
The Secret Double Octopus iPhone solution supports the following authentication methods:
• Push authentication
• OTP authentication
• Apple Watch authentication (Push + OTP)
• BLE authentication (for offline scenarios)
• Show Credentials (in the event that no other options are available, users can enter the temporary password)
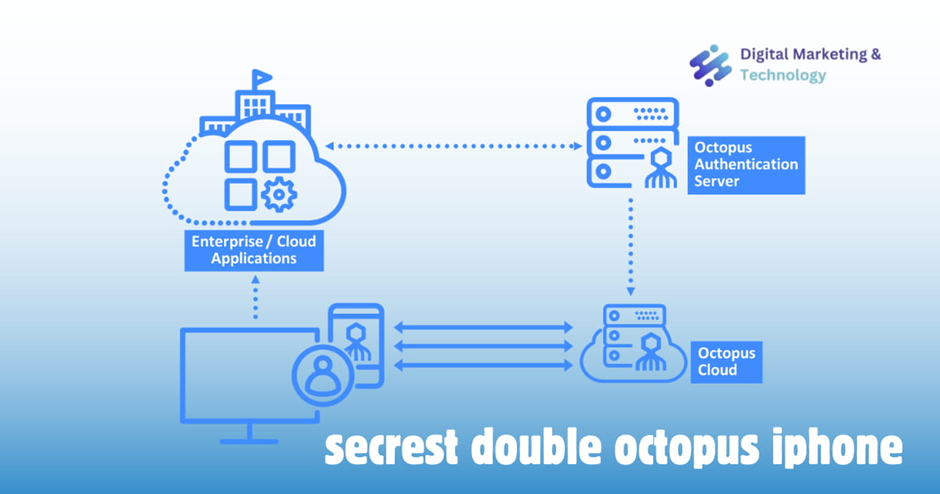
System Architecture
The solution architecture is outlined in the following diagram:
Octopus Authenticator App Installation
The Octopus Authenticator Mobile App can be downloaded from the Apple App Store or Google Play.
Supported Devices
• iOS mobile devices with iOS 10 and above (iPhone 5 or later). We recommend iPhone 5s or later, for use of fingerprint scanning.
• Apple Watch (watchOS 7 and above).
• Android devices with Android 5 and above.
User Enrollment
Octopus Authenticator App requires pre-enrollment to enable users to authenticate and approve transactions. The enrollment process is simple and secured to enroll a user with a specific device.
The user performs enrollment via an invitation email that is generated by the system admin. This email includes a welcome message and the following items:
• Link to download the application (from the App Store)
• Enrollment QR code
• Manual code
• Enrollment link (for use only when clicking on mobile email)
Users can enroll using any of these enrollment options:
• Enroll with the QR code: Users scan the QR code using the Secret Double Octopus iPhone Authenticator App.
• Enroll manually: Users enter the manual code using the Secret Double Octopus iPhone Authenticator App.
• Enroll using the enrollment link: Users open the invitation email on their iPhone and click the Enroll link. This redirects to the Octopus iPhone Authenticator, where users can enroll.
Users receive a confirmation notification upon the first successful enrollment.
Note: For security reasons, the enrollment code expires within a certain timeframe. If the code expires before enrollment, users should contact your organization’s helpdesk or support team for a new enrollment code.
Enrollment Example
The procedure below shows an example of user enrollment using a one-time password (OTP), an enrollment method introduced in version 4.5.0. Users enrolling using password less authentication with the Secret Double Octopus iPhone app will not be asked for an OTP.
To enroll in the system (using OTP):
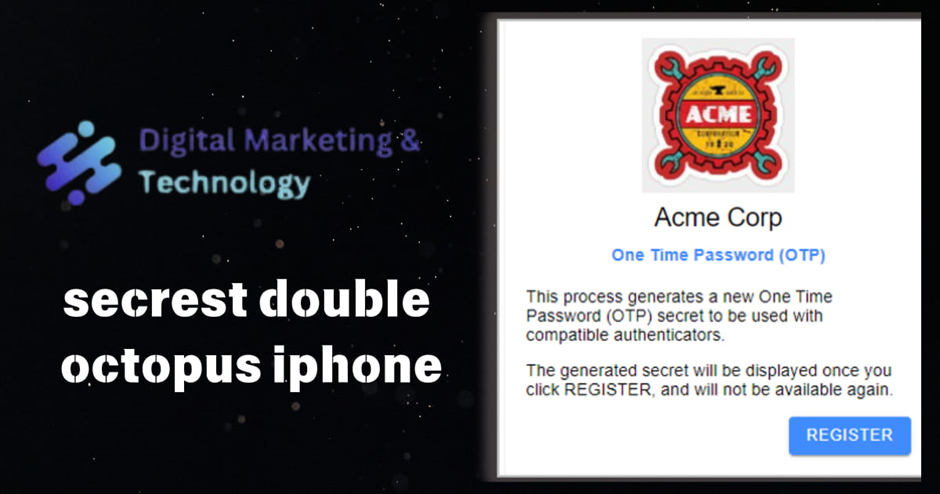
1. From your PC, open the invitation email from Secret Double Octopus and click the enrollment link.
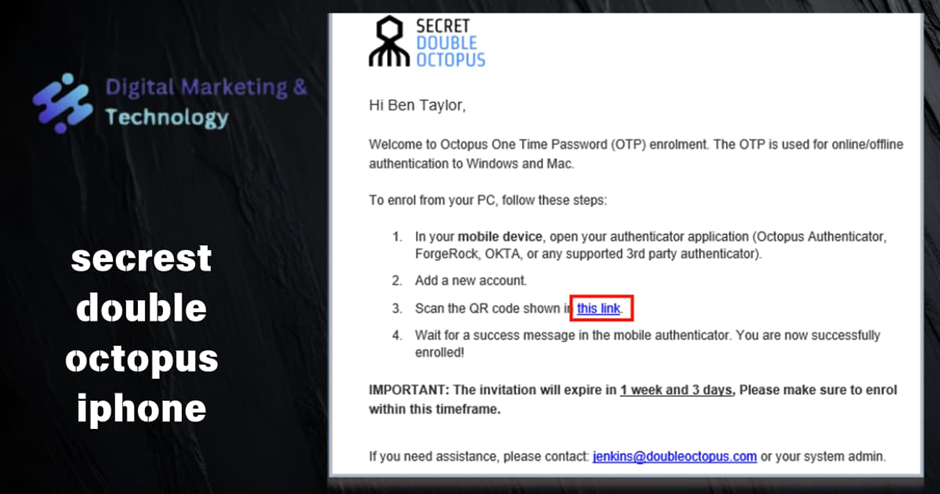
You will be redirected to OTP Authentication Registration in the User Portal.
2. Click Register.
A QR code is displayed in the browser.
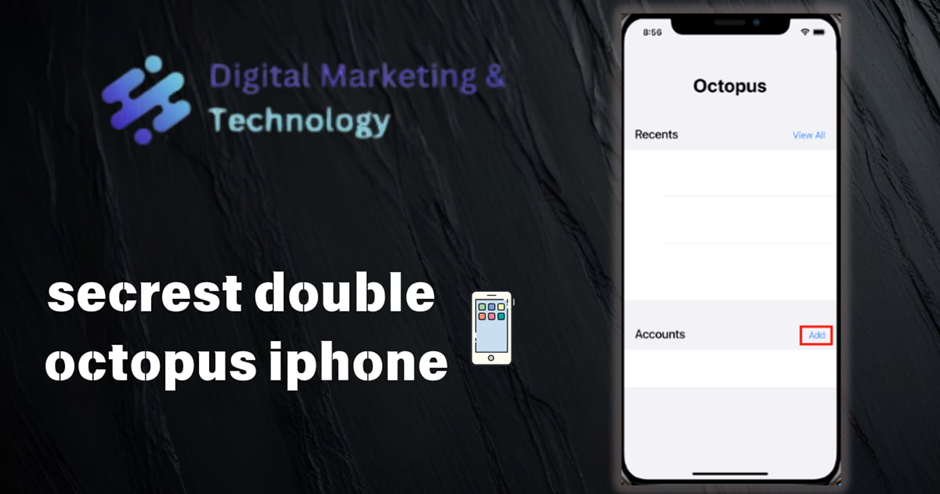
3. Open your authenticator application on your iOS device. (In this example, we use Octopus Authenticator.) On the Home screen, tap Add.
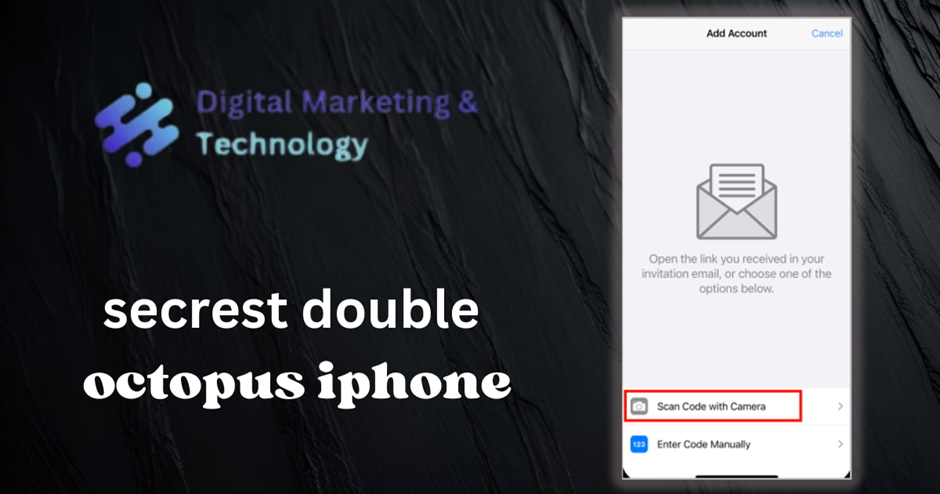
4. On the Add Account screen, tap Scan Code with Camera, and then scan the QR code displayed in your browser.
A confirmation message appears on the Add Account screen.
5. To close the Add Account screen, click OK.
Here’s the revised paragraph with the keyword “secret double octopus iPhone”:
The newly added account is listed on the Home screen of the Secret Double Octopus iPhone app, with the OTP displayed.
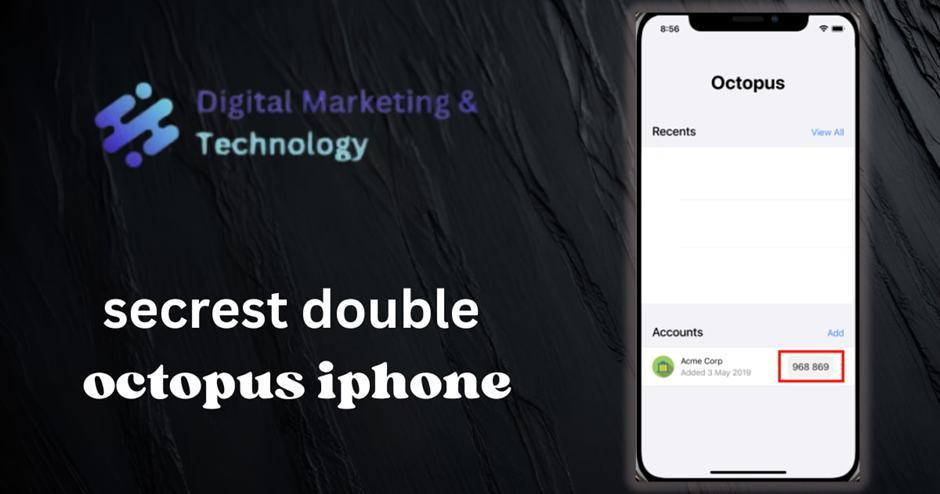
6. Go back to your browser and enter the digits of the OTP code.
After you successfully complete registration, a confirmation message appears, and you can continue with login to the User Portal.

.
Authentication Scenarios
The new authentication flow makes handling authentication requests simpler and quicker. The requests now appear on top of whatever screen is open, and the action buttons are easily reachable with the thumb. In addition, the “loading” time before users can approve the authentication request has been shortened.
Once customers upgrade their Authentication Servers to the latest version, “loading” time is completely removed, and users will be able to approve authentication requests immediately.
Proximity authentications to Windows/Mac over Bluetooth use the same interface as push authentications and are listed in the authentication History screen.
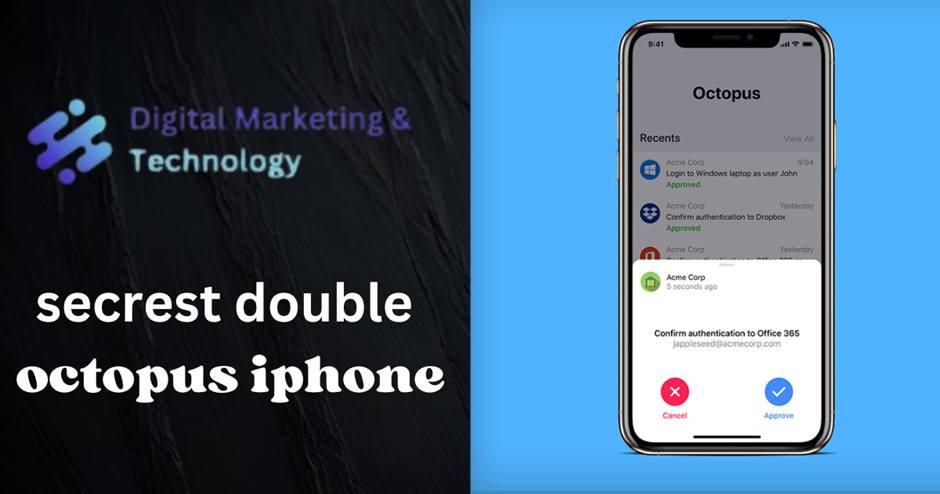
Handling Requests from the Push Notification
When the Secret Double Octopus iPhone app is not open, authentication requests can be handled directly from the push notification by force touching (or long pressing) on the notification bubble. This time-saving feature improves the perceived performance of the app.
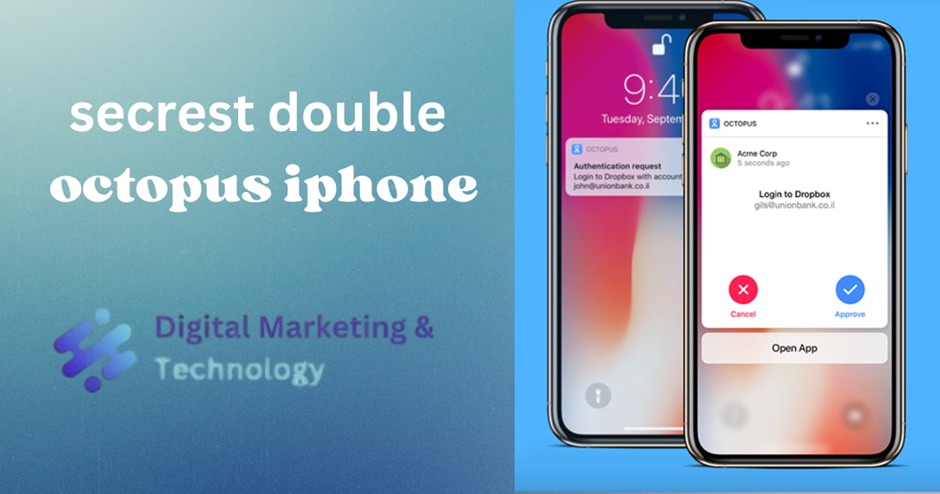
After users tap Approve, they are prompted to complete the authentication process by providing a fingerprint, face ID, or the code/pattern set used to unlock the phone. If more than one identification method is configured, users may choose which method to use.
Note: If an authentication request is received immediately after the phone has been unlocked (within approximately 15 seconds), users are not prompted to provide additional identification.
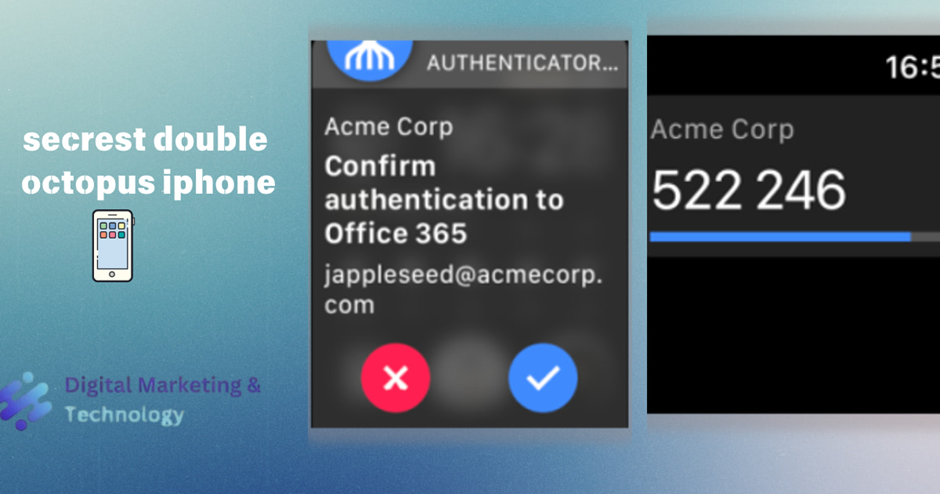
If the phone is locked and pairing with an Apple Watch has been done, the authentication request is automatically sent to the watch. For example:
If the authentication request requires a verification code (e.g., OTP), the code is displayed on the Apple Watch.
First Login from Untrusted Devices
This version of Octopus Authenticator supports Adaptive Authentication, a feature to help prevent user identity hijacking by requiring stronger authentication for login attempts from devices not previously used for Octopus Authentication.
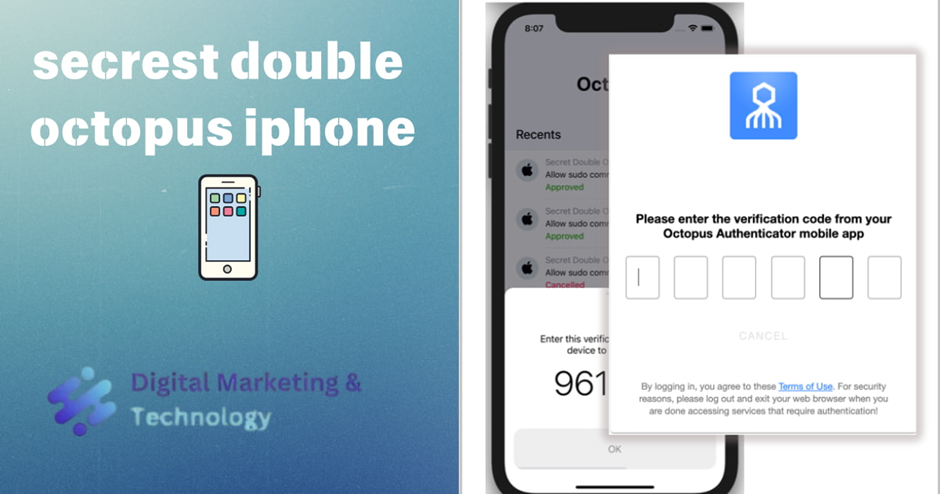
When Adaptive Authentication is enabled, users authenticating for the first time from a unrecognized device (browser/workstation) are required to enter the verification code that is generated and displayed in the Octopus Authenticator mobile app. The verification code is presented immediately after successful authentication.
Following the first successful authentication, users are no longer required to enter a code if the browser or workstation is designated as a Trusted device.
Comprehensive Encryption Protocols Secret Double Octopus employs a comprehensive encryption protocol that safeguards all communications between the Octopus app and the Authentication Server. This ensures that the cloud infrastructure cannot access or alter any authentication data, minimizing potential risks in the event of an attack or system vulnerability.

Mobile App Operation
The interface and navigation options of the Secret Double Octopus iPhone app are designed to benefit the majority of end users, who generally have a single account (enrollment) and do not need to open the app on a regular basis.
Home Screen
The Home screen opens by default when the app is launched. Most functionality is available either directly on the Home screen, or are accessible with a single click.
The Home screen lets users easily view their most recent authentication requests as well as basic information about their accounts. Users can tap View All to open the History screen, which lists all previous authentication requests. Tapping an account opens another screen with additional account details and options.
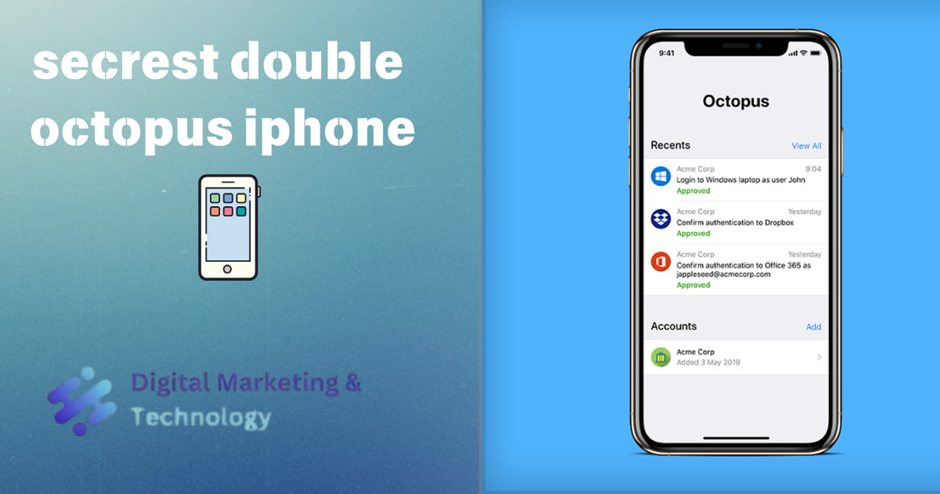
Approved on Another Device
If users have more than one device, the mobile app is immediately updated when an authentication request is approved or denied on another device.
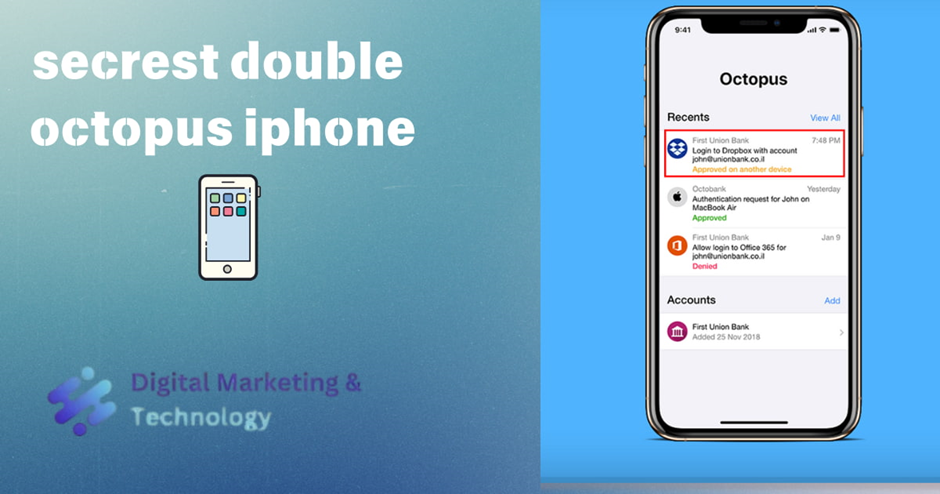
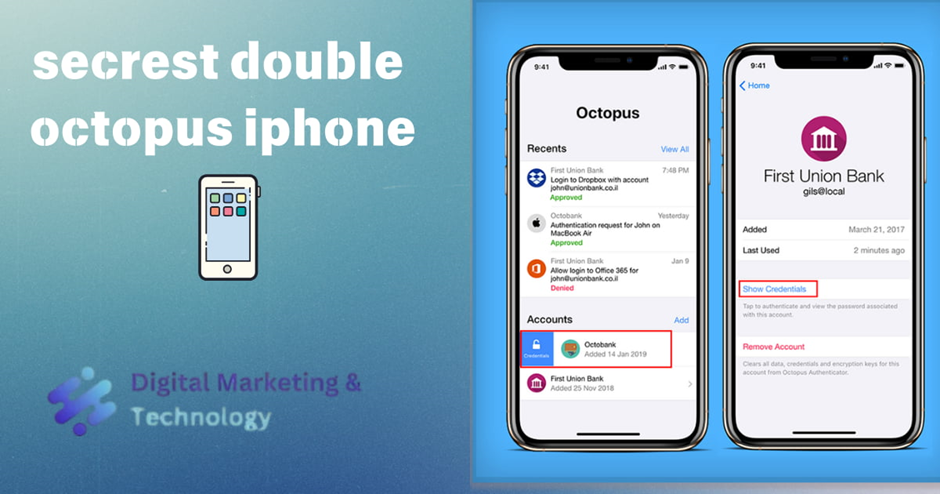
Viewing Account Credentials
The Credentials popup enables users to view and work with passwords and tokens that have been generated for their account(s). The popup is opened from the Home screen by right-swiping across the row of the account and then tapping Credentials.
Alternatively, users can open the popup by tapping the row of the account (to open the Account details page) and then tapping Show Credentials.
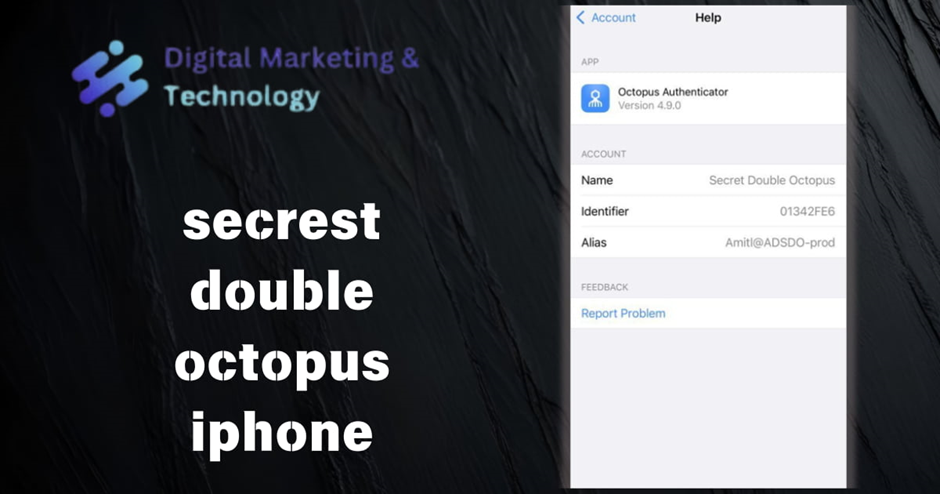
The Feedback portion of the Help screen allows users to easily report issues. When users tap Report Problem, a report which includes account details and a log file, is automatically generated. When users send the report by email, the subject line is prefilled and the company support email appears automatically in the CC list.
Transferring an Account to a New Device
Users who obtain a new phone to replace an old device need to transfer their account to the new device. Transferring an account is done in one of the following ways:
•If the Restore Account feature is supported by the user’s organization, the Restore button appears on the Add Account page. Tapping Restore transfers the user’s account to the new device. (The account on the old device is deleted.)
•If the Restore Account feature is not supported, users need to obtain a new enrollment link from their IT representative and add an account to the new device.
Conclusion
The Secret Double Octopus iPhone Authenticator Mobile App offers a robust, secure, and user-friendly solution for passwordless authentication, enhancing both convenience and security for organizations and users alike. With features such as multi-factor authentication, strong cryptographic security, and seamless integration with mobile devices and desktop environments, the app simplifies the authentication process while minimizing risks from vulnerabilities like MiTM attacks and device tampering. Its support for modern authentication methods, including biometrics and proximity-based login, makes it an ideal choice for securing user accounts across various platforms.
FAQs
How does secret double octopus work?
Secret Double Octopus’ technology is regarded as a universal replacement for passwords, OTPs, physical security keys, smart cards, and other authentication mechanisms. The company uses proprietary phone-as-a-token technology to prevent unauthorized use of systems while preventing identity theft.
What is octopus on iPhone?
Octopus on iPhone or Apple Watch simplifies the way you ride transport and shop in Hong Kong. Breeze through turnstiles or pay at retail outlets just by tapping your iPhone or Apple Watch on Octopus readers.
What is the secret double octopus architecture?
The user sends a login request to the ForgeRock portal. The request goes to the ForgeRock server, which operates Octopus Authentication Node. Octopus Authentication Node sends a REST API call to the Octopus Server. The user is authenticated with Octopus Authenticator.
What is an octopus authenticator?
The Octopus authenticates Window, MAC, and Linux desktop users with self provisioned FIDO2 keys, and includes a certified FIDO2 server for web app authentication out of the box.
What is the double octopus?
Secret Double Octopus is the passwordless authentication solution for the enterprise. We liberate end-users and security teams from the burden of passwords with the simplicity and security of strong passwordless authentication





